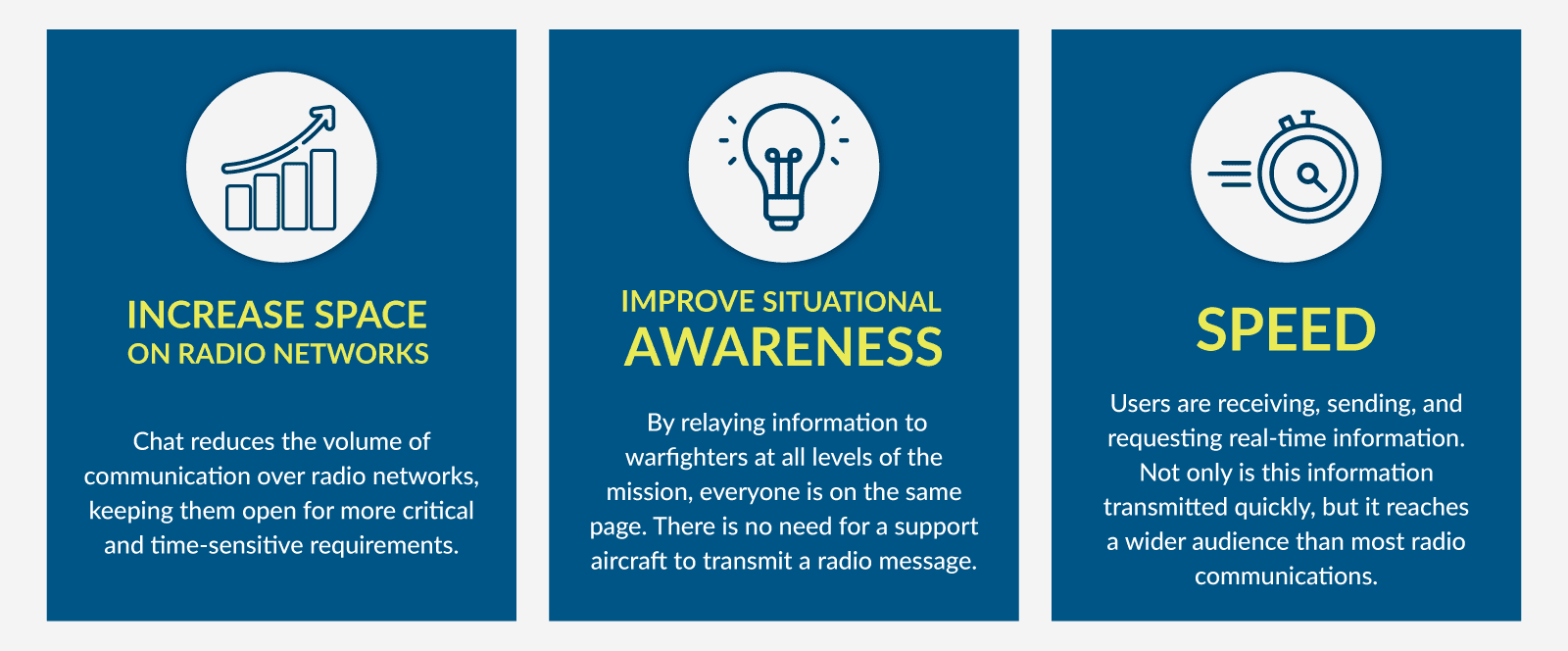
The United States Air Force is going all-in on Agile Combat Employment (ACE), a concept of operations that relies less on large overseas airfield “hubs” and more on smaller “spokes” —tiny, nimble airstrips that enable the Air Force to launch aircraft from anywhere and maneuver faster than ever before.
To see ACE in action, one needs to look no further than the Air Force’s Operation Pacific Iron 2021, an exercise where 800 airmen and 35 aircraft from bases around the Pacific gathered around Guam and Tinian to simulate a large-scale air operation thousands of miles from the nearest continent. The airfield on Tinian was small, manned by just dozens of multi-capable airmen, versus the thousands that populate large hubs such as Pearl Harbor in Hawaii.
The idea of dispersed air operations in austere environments is nothing new. The U.S. operated from numerous improvised airfields during World War II, but Command and Control was always a challenge. Even today, these remote, dispersed forces operate in contested environments where communications are likely to be disrupted or denied altogether.
According to Dr. Mulgund, senior advisor to the Air Force Deputy Chief of Staff for Operations, “tactical level ACE playbook approaches and capabilities must enable dispersed forces to adapt and prevail despite uncertainty, using the best available information to local commanders. This will necessitate shifting the balance between offensive and defensive operations in response to what is achievable in light of available connectivity and logistical support.”
Low SWaP
To rapidly deploy, disperse, and maneuver, the Air Force needs full Command and Control capabilities in all areas of operation in air and on land. Larger C-series aircraft (i.e. a C-17 or C-5) may not be feasible in these small, distributed bases. Therefore, essential C2 capabilities must fit into a smaller C-130 or a CV-22. Additionally, airmen must be able to quickly ruck C2 capabilities and jump them out of an aircraft in the transition to land operations.
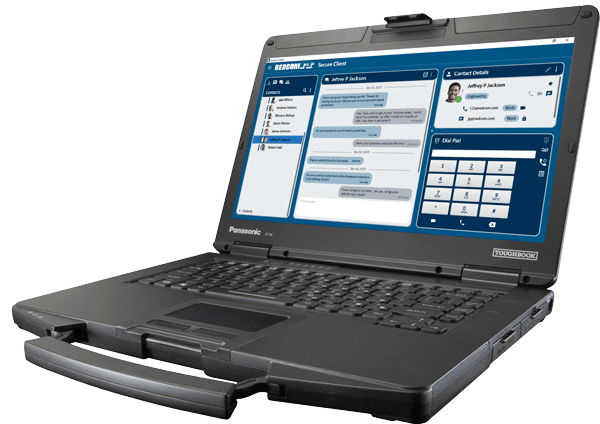
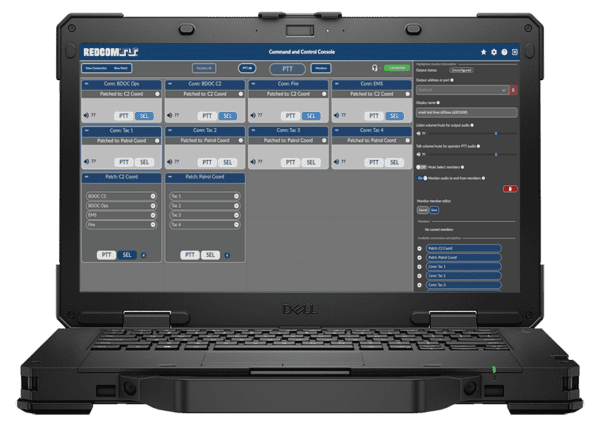
REDCOM meets these requirements with Sigma XRI, a small form factor C2 platform that can be mounted in aircraft, packed, hand-carried, or added to an existing data/comms rack to support all areas of operations.
Interoperability
Airfield ops are joint in nature and will always grapple with the complexities of the combined joint environment. Whether you are conducting a large-scale airfield seizure or inserting a small SOF team into an austere airfield, interoperability with joint forces is critical.
By connecting up to four donor radios directly to the Sigma XRI box, you can instantly bridge the gap between disparate radio networks, endpoints, or frequencies, allowing for seamless communications between Joint and Coalition forces. Additionally, Sigma XRI allows radio users to communicate directly with users on any SIP end device and can even participate in voice conferences.
Resilient Communications
Once an airfield is discovered it is only a matter of time before it is targeted, not only by long-range weapon systems but also directed electronic attacks. Sigma XRI allows the Air Force to leverage multiple communications lines, which is especially critical in scenarios where using whatever means available is crucial to the mission. If one line of communication is compromised the next down the line can be used from IP to Wi-Fi, LTE, SATCOM, UHF, VHF, HF, and TSM.
Command & Control
Regardless of interoperability challenges that arise from joint operations, at all times the crew on the ground must be able to maintain positive control of an active runway. Additionally, they must be able to communicate back to higher C2 nodes so they can receive updates on what’s coming to them and relay back time-sensitive updates that may pose a threat to inbound aircraft.
REDCOM Sigma XRI allows ground forces to maintain a connection with higher command as well as other ground units, all without microwave antennas or satellite shots. In the event a remote airfield becomes a DIL environment, Sigma XRI can act as a stand-alone C2 comms system.
Ease of Use
As demonstrated in the recent Pacific Iron exercise, Air Force personnel are already being tasked with taking on responsibilities that may not be in their primary scope of expertise. Multi-capable airmen will be required to reduce the size of the force required to operate on these small, austere airfields. If a loadmaster with no technical training is going to be asked to run comms, the system must be simple to learn and easy to use. To accommodate, the admin interface on REDCOM Sigma XRI was built intuitively for today’s warfighter — the platform is incredibly easy to learn and operate without the need for field service reps and IT experts.
Conclusion
Effective Command and Control is critical for the Air Force to successfully realize the ACE vision. REDCOM can play an important role in delivering proven C2 solutions to not just the Air Force, but also all branches of our military and coalition partners.
 Español
Español
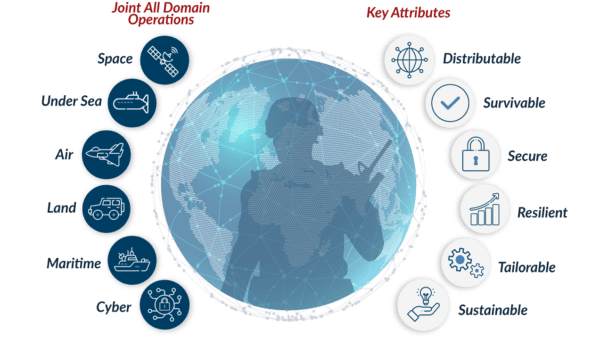 In the C3 modernization effort, the concept of Joint All Domain Command and Control (JADC2) has become front and center.
In the C3 modernization effort, the concept of Joint All Domain Command and Control (JADC2) has become front and center. 
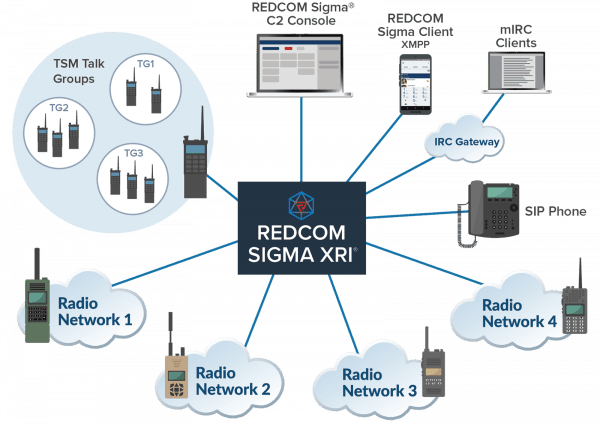

 At the heart of REDCOM’s C2 product family is REDCOM Sigma, a lightweight but powerful command and control software platform.
At the heart of REDCOM’s C2 product family is REDCOM Sigma, a lightweight but powerful command and control software platform.
 REDCOM supplies U.S. and coalition partners with proven and easy-to-use
REDCOM supplies U.S. and coalition partners with proven and easy-to-use