The U.S. Army defined a suite of open architecture standards to reduce C5ISR (command, control, computers, communications, cyber-defense, intelligence, surveillance, and reconnaissance) demands. These standards will address SWaP (System Size, Weight, and Power) requirements and provide commonality across multiple platforms by sharing hardware and software components. This architecture defines CMOSS, (C5ISR Modular Open Suite of Standards), driving a change in how hardware and software interact.
Existing networks and systems work through multiple types of hardware and software running on different systems, which are often unable to communicate with one another. If one component or subcomponent fails, it would need to be replaced manually to continue communication. CMOSS will allow for all resources to be shared and swapped, usually in real-time. This would lead to a consolidation of hardware such as radio boards, GPS, control boards, and computer boards into one box. CMOSS will continue to push industry innovation with a standards-based approach, instead of relying on proprietary standards.
Key Benefits and Advantages of CMOSS
CMOSS has the potential to revolutionize communications at the tactical edge:
- Initial implementation costs will prove to be more cost-effective as upgrade capabilities reduce the need for manual repair and replacement of failed or obsolete components.
- It will be easier to keep pace with commercially available solutions, reducing integration challenges and costs. With the open architecture structure, multiple vendors can create boards for the CMOSS platform.
- CMOSS dramatically reduces data stovepipes, making the sharing of hardware between systems simpler where appropriate. This enables optimized integration and utilization of all the communications, collection, and management information available across any platform.
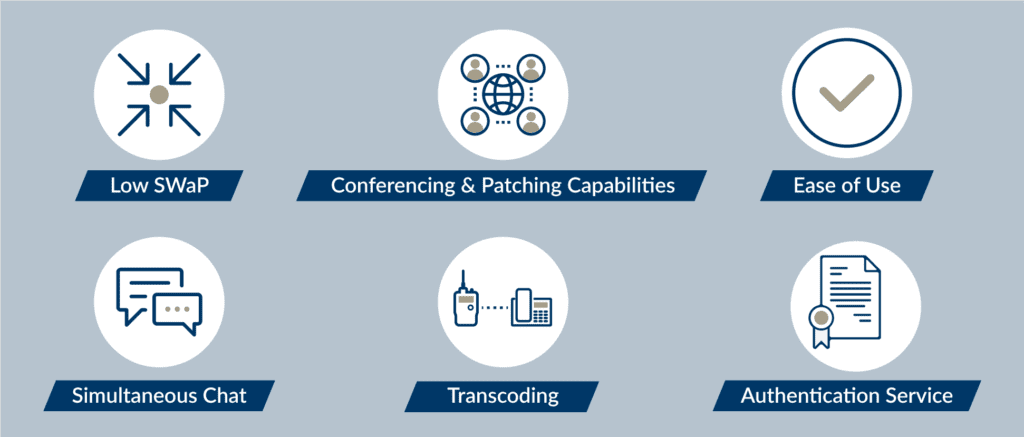
REDCOM’s path forward with CMOSS
While CMOSS has many benefits and advantages, there are still gaps that can be filled:
- Low SWaP. The current systems in place are high in SWaP, and REDCOM Sigma will not only allow for voice and chat management, which current systems do not have, but it will reduce hardware and software footprint. REDCOM will provide a bridge between new CMOSS components and existing legacy components, obviating the need to integrate CMOSS gracefully into the data, and communications architecture.
- Conferencing and patching capabilities. REDCOM provides important voice, chat, and video conference management software — services that are not on the near-term roadmap for CMOSS. Our conferencing engine is endpoint agnostic, which means any endpoint can be connected together, from SIP desk phones and smartphones to radios and satcom devices.
- Ease of Use. REDCOM Sigma has a simplified user interface. Systems that are easy to learn will reduce time spent in training and reduce the need for direct involvement of vendors on the battlefield. Recently REDCOM visited Camp Lejeune and trained Marines in less than two days, a massive reduction of training commitment that allowed warfighters to attend to their primary objectives with minimal investment in training time. Not only was training quick, but the interface was so easy to use and understand that the Marines felt confident enough to train others.
- Simultaneous Chat. Our Chat Manager allows management of multiple chat sessions simultaneously in an environment where multiple users need to touch base frequently and urgently. Simplified management translates into increased speed and safety.
- Transcoding. REDCOM Sigma features the built-in ability to handle radio to VoIP transcoding. Sigma will be able to transcode between common radio codecs such as MELPe and GSM-AMR and VoIP CODECs such as G.729 and G.711. This reduces the need for having DSP resources or additional CPU boards for handling transcoding.
- Authentication Service. REDCOM has been studying the principles of Zero Trust Architecture. REDCOM is looking to help produce a zero-trust network that is operationally secure at the enterprise level while prioritizing a zero-trust architecture in forward-deployed environments, bringing security to even the most fringe areas of the DoDs operations.