It finally looks like the U.S. is ready to do something to combat unwanted robocalls. The Senate has passed the TRACED Act, which stands for Telephone Robocall Abuse Criminal Enforcement and Deterrence. This new legislation would raise the fines the FCC is permitted to levy on robocallers while also increasing the statute of limitations for violations to three years. The bill would also create an interagency task force to address the problem, and push service providers to implement call authentication systems.
“As the scourge of spoofed calls and robocalls reaches epidemic levels, the bipartisan TRACED Act will provide every person with a phone much-needed relief,” said U.S. Senator Ed Markey. “It’s a simple formula: call authentication, blocking, and enforcement, and this bill achieves all three.”
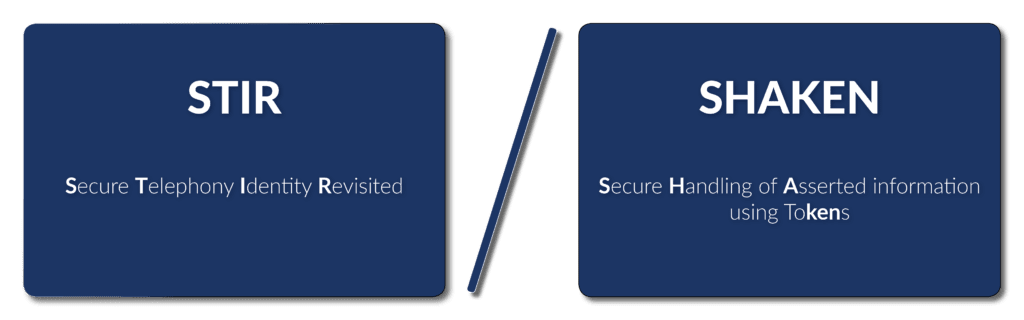
A key mandate from the bill is the requirement that carriers work together to implement call authentication technology, and it looks like STIR/SHAKEN could be the preferred method. STIR is short for Secure Telephony Identity Revisited, while SHAKEN stands for Secure Handling of Asserted information using Tokens.
How does STIR/SHAKEN work?
Essentially what STIR/SHAKEN does is use digital certificates, based on common public key cryptography techniques, to ensure the authenticity of the call. Here’s how STIR/SHAKEN works in the world of telephony:
- When a call is initiated, a SIP INVITE is received by the originating service provider.
- The originating service provider verifies the call source and number to determine how to confirm validity.
- Full Attestation (A) — The service provider authenticates the calling party AND confirms they are authorized to use this number. An example would be a registered subscriber.
- Partial Attestation (B) — The service provider verifies the call origination but cannot confirm that the call source is authorized to use the calling number. An example would be a calling number from behind an enterprise PBX.
- Gateway Attestation (C) — The service provider authenticates the call’s origin but cannot verify the source. An example would be a call received from an international gateway.
- The originating service provider will now create a SIP Identity header that contains information on the calling number, called number, attestation level, and call origination, along with the certificate.
- The SIP INVITE with the SIP Identity header with the certificate is sent to the destination service provider.
- The destination service provider verifies the identity of the header and certificate.
The complete solution
STIR/SHAKEN is a great start and absolutely should be part of the overall robocall solution, but it is not the end all be all. STIR/SHAKEN only applies to SIP-initiated calls and must be supported by the carriers at both ends of a call. Thus, scammers could conceivably get past STIR/SHAKEN simply by originating their robocalls on a TDM network.
REDCOM’s Personalized Call Screening software already includes full STIR/SHAKEN support, but it goes much further than that. Our “best of all worlds” approach means that we also enable several other layers of protection including:
Reputation Scoring: We integrate directly with TNS Call Guardian, an industry-leading solution that uses real-time crowd-sourced data to identify abusive or unlawful callers.
White list/Black list: We allow carriers and subscribers to create their own white- and black-lists, which gives end users far more control over protecting their phone numbers.
Recorded Greetings: Requires the calling party to record a greeting, which is played to the called party before accepting the call.
Audio CAPTCHA: requires the caller to respond with dialed digits, which stops robocalls dead in their tracks.
Service providers that implement REDCOM’s Personalized Call Screening software will be in full compliance with the pending TRACED Act, with the option of going above and beyond STIR/SHAKEN by implementing any number of these customizable call blocking tools.

 Español
Español