Pa$$w0rd C0mpl3xity!
Password complexity. What type of emotion does that simple phrase invoke? Do you shudder with trepidation at the thought of having to come up with a convoluted string of characters that comply with a myriad of rules? Do you gasp at the shock of not remembering your password to log into your bank account? Passwords can certainly be complex, and not in a good way. Fortunately, the idea of complex passwords is changing, and that’s a good thing.
In 2003 the National Institute of Standards and Technology (NIST) published the NIST Special Publication 800-63. Among other things, this document provided guidelines for password requirements. The recommendations for sufficiently complex passwords included the following:
- Must be a minimum of eight characters
- Must include a mix of uppercase letters, lowercase letters, numeric, and special characters
- Must not contain sequential characters from the username
- Must not contain sequential characters from the user’s first or last name
- Must change the password periodically (typically every 90-180 days)
- Must not reuse passwords (typically within the last eight)
As a result, passwords such as Pa$$w0rd!1 became commonplace. And therein lies the problem. We, as humans, are predictable. To overcome the awkwardness of the rules, we began using recognizable patterns. Worse yet, when it came time to change our password, the natural migration was to change Pa$$w0rd!1 to Pa$$w0rd!2. Again, predictable.
In a recent interview with the Wall Street Journal Bill Burr, the author of NIST SP 800-63, admitted that much of what he did was wrong. To be fair, he was flying somewhat blind. He looked for research data regarding password security and came up empty-handed. Empirical data simply didn’t exist at the time. So, he set about creating the recommendations and did what most of us would likely have done in the same situation. He set about creating some rules that made it sound as if it would result in hard to crack passwords. The unfortunate reality is that this resulted in passwords that were hard for humans to remember, but easy for computers to crack.
In June 2017 NIST SP 800-63 was updated and the password complexity recommendations were completely rewritten and simplified. These simplified requirements emphasize password length and memorability above all else. Longer passwords are harder to crack and we are less likely to use Post-it® notes to write down passwords. The updated password recommendations include:
- Longer passwords (typically up to 64 characters)
- A mix of character types is no longer recommended
- No need to change passwords unless there is evidence that it has been compromised
- Must be compared to a list of known bad passwords
- Must not contain the associated username
- Must not contain the user’s first or last name
Given the new recommendations, the general consensus is that a password should consist of four random words strung together. There is no need for a mix of character types, so the password would be made up of all lowercase letters without spaces. For example, coffeediplomaeaglephone.
Randall Munroe, cartoonist, and author of the xkcd webcomic put together a comparison on the strength of the two recommendations. He calculated the time needed to crack passwords from each of the two methods. He chose Tr0ub4dor&3 and correcthorsebatterystaple as the subjects of the analysis. He calculated that it would take a short three days to crack Tr0ub4dor&3 but a whopping 550 years would be needed to crack correcthorsebatterystaple. His results were verified as accurate by computer security specialists.
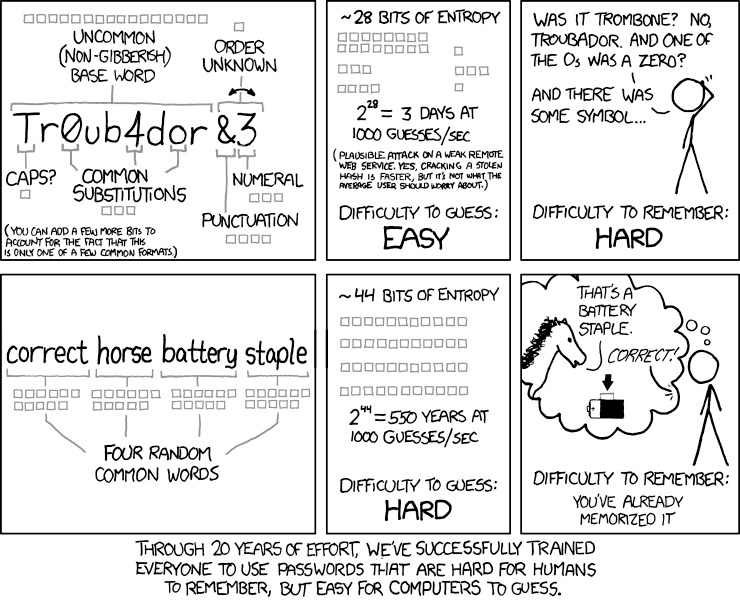
The good news is NIST recommendations have evolved to allow for passwords that are less frustrating to set up, easier to remember, and harder to crack. The bad news is that it takes time for the word to get out, have the recommendations adopted, and software developers to implement the changes.

 Español
Español