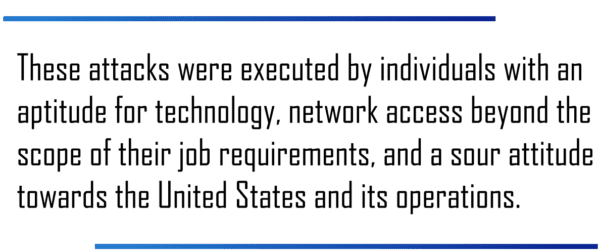
 he most egregious security breaches in recent United States history were the direct result of the actions of individuals with both insider access and malicious intent. Some of these security breaches, namely the Manning and Snowden incidents, caused detrimental damage that the United States is still recovering from. Though devastating, these attacks were not executed by individuals with profound technological ability or intellectual prowess but by individuals with an aptitude for technology, network access that spanned far beyond the scope of their job requirements, and a sour attitude toward the United States and its operations.
he most egregious security breaches in recent United States history were the direct result of the actions of individuals with both insider access and malicious intent. Some of these security breaches, namely the Manning and Snowden incidents, caused detrimental damage that the United States is still recovering from. Though devastating, these attacks were not executed by individuals with profound technological ability or intellectual prowess but by individuals with an aptitude for technology, network access that spanned far beyond the scope of their job requirements, and a sour attitude toward the United States and its operations.
Investigation of these incidents revealed ample evidence of the actors’ negative sentiments toward the United States – information that was known and in some cases, broadcasted publicly long before the insider attacks occurred. Records have also shown that, for both Chelsea Manning and Edward Snowden, questions of mental fortitude and disregard for proper operating procedures and the chain of command have been present throughout their professional careers.
Analyses of these attacks and statements made by their perpetrators have revealed that their success did not come from meticulous planning or novel methods of exfiltration but from the victims’ failure to adhere to fundamental principles of cybersecurity, a generally loose culture surrounding security, and a lack of tools to monitor internal network traffic. Improving upon these three concepts would have prevented these detrimental insider attacks and can prevent similar breaches from occurring in the future.
 he Manning incident involved the unauthorized release of sensitive information pertinent to the wars in Iraq and Afghanistan and a host of international diplomatic relationships. Found guilty of multiple violations of the Espionage Act in 2013, Private Chelsea (formerly Bradley) Manning collected troves of sensitive data, personnel lists, and diplomatic cables for the benefit of and, in some cases, at the behest of WikiLeaks. At the beginning of her military career, Manning recounted to known hacker Adrian Lamo her hardships in finding commonality between herself and other service members, her overall failure to assimilate into the Army culture, and her sympathies for terrorist actors. Manning also reportedly “lashed out at fellow soldiers” soon after basic training, and her direct supervisors voiced concerns about whether she would be able to handle the mental stress of combat deployment. However, these concerns did not prevent Manning from having access to sensitive networks and using that access to carry out her now infamous data exfiltration campaign.
he Manning incident involved the unauthorized release of sensitive information pertinent to the wars in Iraq and Afghanistan and a host of international diplomatic relationships. Found guilty of multiple violations of the Espionage Act in 2013, Private Chelsea (formerly Bradley) Manning collected troves of sensitive data, personnel lists, and diplomatic cables for the benefit of and, in some cases, at the behest of WikiLeaks. At the beginning of her military career, Manning recounted to known hacker Adrian Lamo her hardships in finding commonality between herself and other service members, her overall failure to assimilate into the Army culture, and her sympathies for terrorist actors. Manning also reportedly “lashed out at fellow soldiers” soon after basic training, and her direct supervisors voiced concerns about whether she would be able to handle the mental stress of combat deployment. However, these concerns did not prevent Manning from having access to sensitive networks and using that access to carry out her now infamous data exfiltration campaign.
The prevailing factor in the success of Manning’s exfiltration tactics was the loose security culture surrounding the sensitive networks and their resources. In the presence of other network operators, Manning was able to download “thousands of classified significant activities (SIGACTS)” pertaining to Iraq and Afghanistan to a CD. Her ability to collect this data on a physical medium prompted more exfiltrations in a similar fashion, sometimes for the benefit of Julian Assange and WikiLeaks. In fact, Manning found the security culture to be so relaxed that she created a tasker on her DoD workstation that reminded her to acquire the Global Address List from the United States Forces-Iraq Microsoft/Outlook Server (USF-GAL), a trove of 74,000 email addresses. As a further testament to the loose security culture in Manning’s operating environment, she told Lamo that transferring data to unmarked CDs was actually quite common within the workspace, claiming “we transferred so much data” and that “everyone did” participate in data transfer this way.
Manning has actually credited this loose culture with providing her the opportunity to perform this massive amount of data extraction, as other network operators were often preoccupied with their own precipitous activities in the workspace. Manning has cited “weak servers, weak logging, weak physical security, weak counter-intelligence, [and] inattentive signal analysis” as the main contributors, the “perfect storm” to the success of her attack. The lack of both proper access controls and an internal traffic monitoring system also aided Manning in this campaign of information leakage.

For example, Manning often reached data that existed outside the scope of her operations using her credentials alone. Manning was also able to introduce third-party software called “wget” to her workstation, which she used to download hundreds of thousands of diplomatic cables, some of which eventually fell into the hands of WikiLeaks operatives. Had any sort of traffic monitoring system been in place, this anomalous insider behavior, including the introduction of outside software and unusual download patterns, would have been easily detected.
![]() hen considering the circumstances of the Snowden attack, many parallels can be drawn to the Manning situation. Leading up to Edward Snowden’s infamous data exfiltration campaign against the NSA, Snowden experienced clashes with direct supervisors and repeated failures to assimilate with his coworkers, similar to Manning’s struggles in the Army. While Snowden was working for the CIA in 2007, Snowden’s immediate supervisor recounted his unwillingness to “recognize the chain of command” and inability to “embrace the CIA culture.” While this alone may not have provided sufficient cause for concern about Snowden, current evidence suggests that Snowden fabricated portions of his education and work experience. This information was not revealed when he was employed by a major defense contractor for the NSA, as Snowden’s background investigation was “incomplete.” This unfinished background check failed to verify a self-reported “past security violation” and was unable to develop sufficient character witnesses. Had this investigation into Snowden’s history been completed, his consistent problems with leadership, failure to adopt working cultures of U.S. agencies, and untrustworthy character would have been revealed, possibly preventing him from receiving the clearances that proved integral to his attack.
hen considering the circumstances of the Snowden attack, many parallels can be drawn to the Manning situation. Leading up to Edward Snowden’s infamous data exfiltration campaign against the NSA, Snowden experienced clashes with direct supervisors and repeated failures to assimilate with his coworkers, similar to Manning’s struggles in the Army. While Snowden was working for the CIA in 2007, Snowden’s immediate supervisor recounted his unwillingness to “recognize the chain of command” and inability to “embrace the CIA culture.” While this alone may not have provided sufficient cause for concern about Snowden, current evidence suggests that Snowden fabricated portions of his education and work experience. This information was not revealed when he was employed by a major defense contractor for the NSA, as Snowden’s background investigation was “incomplete.” This unfinished background check failed to verify a self-reported “past security violation” and was unable to develop sufficient character witnesses. Had this investigation into Snowden’s history been completed, his consistent problems with leadership, failure to adopt working cultures of U.S. agencies, and untrustworthy character would have been revealed, possibly preventing him from receiving the clearances that proved integral to his attack.

In addition to this undiscovered information about his past, Snowden’s job position provided him with top-secret clearance and wide-reaching access within NSA networks – access privileges which already far exceeded the requirements for him to fulfill his job responsibilities. Snowden eventually went on to employ social engineering tactics to persuade other employees to provide him with their credentials, allowing him access to previously unavailable data and projects. Snowden utilized this all-encompassing, unmonitored network access to download data en masse. From secret NSA project files to data within the personal storage drives of other NSA employees, Snowden performed actions that should have been leagues beyond his access capabilities.
Not only were Snowden’s privileges too extensive, but there were also no mechanisms in place to monitor unusual traffic, such as mass downloads of unrelated files or accessing the personal data storages of others, despite former NSA technical director Bill Binney asserting that it was possible for this technology to be in place long before Snowden worked there. Beyond these oversights pertaining specifically to the network, Snowden lived mostly in Honolulu at the time and found himself at an advantage with his physical location. He often accessed the NSA network remotely, via a “thin-on-thick” machine, during hours in which on-site NSA employees had already finished work for the day. Outside individuals operating within the NSA network with near unlimited access, no oversight, and no other employees to interact with capitalizes the necessity of an in-house traffic monitoring system. But, according to Binney, this is unlikely to happen due to the security culture within the NSA. “Spies don’t want to be spied on,” Binney affirmed in a 2014 NPR interview, also suggesting the NSA has no plans to practice in-house traffic monitoring in the future.

 lthough these incidents were unrelated, they were detrimentally successful in exploiting the same weaknesses. Security culture, or the attitude surrounding security of data and assets amongst its day-to-day operators, was largely exploited by Manning. Manning leveraged a relaxed security culture to collect data from sensitive networks on CDs. Manning then took this data and uploaded it to her own personal computer before handing it over to WikiLeaks. Despite exfiltrating this data during the day and in plain sight, not one question was raised about Manning’s actions.
lthough these incidents were unrelated, they were detrimentally successful in exploiting the same weaknesses. Security culture, or the attitude surrounding security of data and assets amongst its day-to-day operators, was largely exploited by Manning. Manning leveraged a relaxed security culture to collect data from sensitive networks on CDs. Manning then took this data and uploaded it to her own personal computer before handing it over to WikiLeaks. Despite exfiltrating this data during the day and in plain sight, not one question was raised about Manning’s actions.
Both Manning and Snowden found success in the lack of thorough investigation of their personal histories. Concerns of Manning’s mental fortitude, inability to assimilate with other service members, and regular conflicts with other soldiers were hardly considered before access to sensitive networks was given to her. Likewise, Snowden’s own problematic history was not analyzed before his attainment of top-secret security clearance and unfettered access to the NSA internal network. Snowden’s general disrespect for authority, history of support for actors like Manning, previous security incidents, and untrustworthy character were nonfactors in the decision to allow Snowden unmonitored access to the internal network of the NSA.

Manning and Snowden both benefitted from the lack of a monitoring system, which enabled them to collect colossal amounts of data in short periods of time. The lack of monitoring also enabled them to reach data that did not pertain to their day-to-day operations and, in the case of Manning, install an unauthorized application that allowed WikiLeaks operatives access to information within SIPRNet. Snowden saw optimal assistance in the oversight of his access privileges, which “far exceeded the access required to do his job,” and from coworkers who were vulnerable to his social engineering efforts. This fact coupled with the lack of internal monitoring and Snowden’s regular network access outside of normal working hours allowed his exfiltration campaign to carry out flawlessly. These factors that contributed to the successes of both Manning and Snowden stem from systematic problems within the current culture surrounding our security.
![]() n the aftermath of these incidents, analyses have revealed the lack of technical complexity and relatively straightforward attack methods. These attacks found their successes in exploiting weaknesses in the practice of fundamental principles of cybersecurity. Cutting-edge data analytics or a top-notch AI solution will have no chance of stopping the next Manning or Snowden if they have already been given the access needed to haul the servers out of the building. The next major insider breach will be stopped by individuals and community – individuals who practice security and a community that promotes and discusses the importance of it. Becoming brilliant in the basics of security, promoting a healthier security culture, and engaging the community will counter insider threat before it has a chance to begin.
n the aftermath of these incidents, analyses have revealed the lack of technical complexity and relatively straightforward attack methods. These attacks found their successes in exploiting weaknesses in the practice of fundamental principles of cybersecurity. Cutting-edge data analytics or a top-notch AI solution will have no chance of stopping the next Manning or Snowden if they have already been given the access needed to haul the servers out of the building. The next major insider breach will be stopped by individuals and community – individuals who practice security and a community that promotes and discusses the importance of it. Becoming brilliant in the basics of security, promoting a healthier security culture, and engaging the community will counter insider threat before it has a chance to begin.











