Introduction
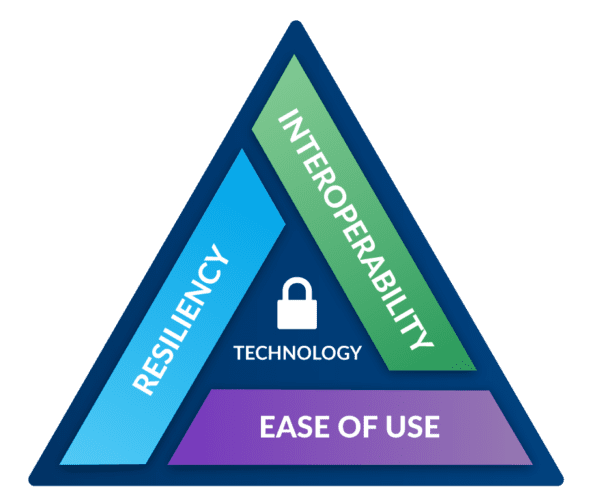
REDCOM takes a holistic, multi-layer approach to security that goes beyond typical measures such as encryption and validation. Take a look at Secured Communications paper that discusses REDCOM’s stance on overall mission security, which necessitates a strong focus on encryption, resiliency, interoperability, and ease of use.
The United States armed forces are facing increased cyber capabilities from our near-peer adversaries, who fully realize how vital communication is to every facet of modern military operations. So, they are becoming more proficient in techniques such as hacking, signal jamming, and disruption.
In today’s information-intense domain, security is absolutely critical to the success of the mission. But what exactly does the term “security” mean? REDCOM has a much broader interpretation of security because we focus on the overall security of the mission.
Missions can be compromised by a variety of factors, including:
- Single points of failure.
- Slow boot-up/tear-down times.
- Interoperability challenges.
- System complexity.
Technology
The above scenarios are clearly security concerns, but they have nothing to do with encryption or validation. This is why REDCOM takes a holistic, multi-layer approach to security. We build security into all of our products from the start.
REDCOM solutions are:
- Standards-based. REDCOM builds our products to industry standards, ensuring interoperability with a variety of transmission paths, gateways, and endpoints. Users are never locked into proprietary end instruments.
- Encrypted. We invest in the latest forms of encryption, and allocate significant R&D efforts towards the development of next-generation encryption and authentication technologies.
- Compliant. REDCOM maintains compliance with numerous DISA and NIAP requirements.
- Tested & Certified. REDCOM meets stringent session controller functionality and interoperability requirements as defined in the Unified Capabilities Requirements (UCR). We rigorously test our products with the Joint Interoperability Test Command (JITC) to ensure our solutions are certified on the DoDIN Approved Products List. REDCOM Sigma® and the REDCOM Secure Client for Android have passed FIPS 140-2 validation testing, meaning that we can provide standardized, secure solutions for government agencies by appropriately handling SBU data.
Want to know more about REDCOM’s stance on securing the mission at the tactical edge? Check out a recent webinar, hosted by REDCOM Government Account Manager, Courtney Stiles.











