The global pandemic has shed light on the shortcomings of critical infrastructure across industries and uncovered significant vulnerabilities in current systems. One lesson to take from this pandemic is the importance of proactively examining essential systems for potential vulnerabilities.
This practice is especially important in the telecommunications sector, which houses several critical sites and services that enable life-saving communications. As an exercise, REDCOM took a look at one of these systems, the Wireless Emergency Alert System or WEA (now known as the Presidential Alert System).
WEA
If you have ever received an amber alert or severe weather alert directly on your smartphone, you’ve seen WEA in action. WEA is the system responsible for driving critical announcements to all available LTE devices in a target area. While this system is largely seen as a benefit to communities, there is an opportunity for abuse within the WEA by malicious parties with the appropriate technical skill and motivation.
Past abuse of WEA
In 2018, a state-wide false alarm occurred in Hawaii, where residents were told that a ballistic missile was en route to Oahu. This incident was the result of miscommunication between workers at the Hawaii Emergency Management Agency (HEMA) and general human error. This alert was not deemed a false alarm for fifteen minutes before Hawaii’s governor David Ige made the announcement on Twitter. HEMA did not broadcast a corrective message until thirty minutes had passed.
 In the hour after receiving the alert, residents were in a panic and attempting to flee or shelter at any cost. Honolulu EMS saw a doubling in its calls for assistance, with some of the more notable calls detailing heart attacks and vehicular accidents. With just an accidental misuse of the WEA system causing such damage, panic, and mayhem, one’s thoughts turn to the worst-case scenario: What damage could be done through a widespread, coordinated attack using the WEA System?
In the hour after receiving the alert, residents were in a panic and attempting to flee or shelter at any cost. Honolulu EMS saw a doubling in its calls for assistance, with some of the more notable calls detailing heart attacks and vehicular accidents. With just an accidental misuse of the WEA system causing such damage, panic, and mayhem, one’s thoughts turn to the worst-case scenario: What damage could be done through a widespread, coordinated attack using the WEA System?
Understanding how WEA works
WEA alerts can be sent from a variety of Emergency Operations Centers (EOCs) – local and state EOCs have the power to send WEA alerts to their corresponding areas, while government agencies can send out nationwide alerts. A high-level view of the WEA system architecture can be seen below.
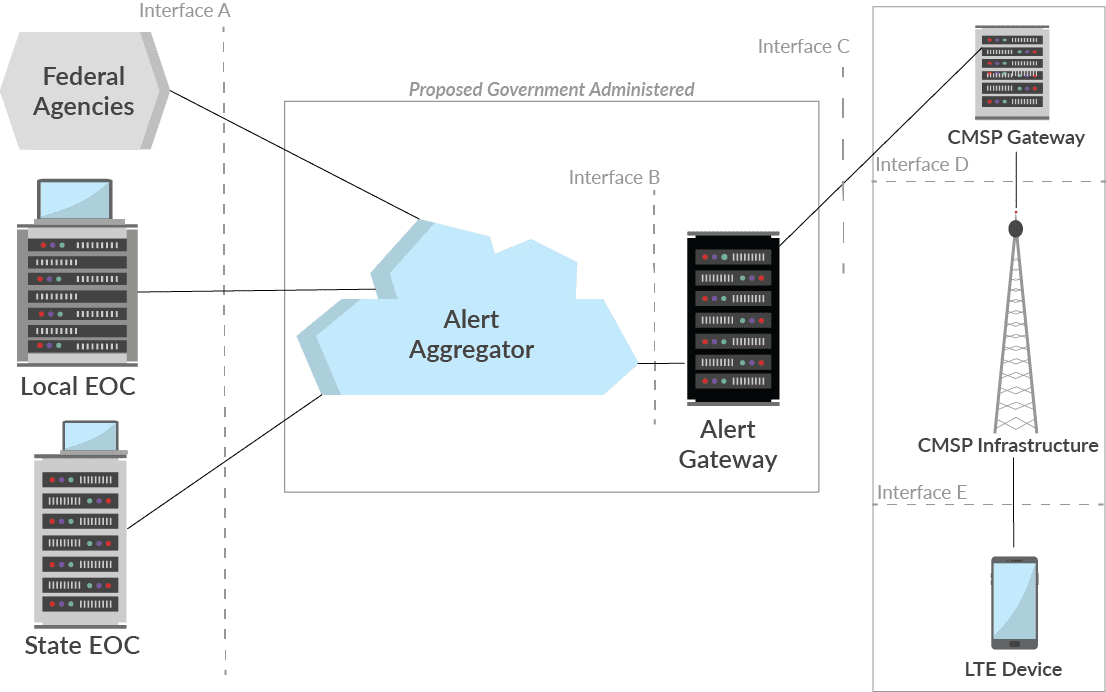
Although not detailed in this image, the act of issuing a WEA alert appears fairly secure. WEA alerts must be submitted through a portal that requires a certified operator’s credentials (Mead, 2016). This alert must then be signed by a second operator before the alert can be sent to the Federal Alert Aggregator, further inspecting and authenticating the alert. If an alert is authenticated, it is sent through an Alert Gateway, where the alert will then be distributed according to who issued it; to the areas which the incident has/will affect, etc. Residents in the affected area then receive a WEA alert on their smart devices which informs them of the event at hand.
It is this stage of distribution where the major vulnerability lies for the WEA system. According to researchers at the University of Colorado at Boulder (UCB), a malicious actor would only need to construct a makeshift cellular tower and know how to impersonate the alert format to distribute false WEA alerts to citizens in a given area. This vulnerability is due to the use of less-secure LTE mechanisms rather than more traditional authentication-based messaging mechanisms.
Hypothetical cyber attack
Because the goal of WEA messages is to broadcast to as many devices as possible, a threat actor with a makeshift cell tower only needs to know the message format and the LTE channel to send the faulty message to – any LTE device will then receive the message if they are in the range of the false tower. The formatting and band information are available and accessible through open-source and commercial-of-the-shelf (COTS) means.
Given this information, it is unlikely that a malicious actor would be able to spoof a nationwide alert through the WEA system. However, it is plausible that a team of actors can distribute false messages to a few key populated areas to incite panic and create turmoil.
 If this attack were successful, and a few major cities were hit simultaneously, there could be substantial damage and loss of life. There could certainly be a period of time of total chaos if the message were severe enough and distributed to enough people. Depending on the content of the false alert, other critical resources may become unavailable due to investigating the situation (e.g., a false bomb threat in a crowded stadium may draw more police and EMS resources than other incidents).
If this attack were successful, and a few major cities were hit simultaneously, there could be substantial damage and loss of life. There could certainly be a period of time of total chaos if the message were severe enough and distributed to enough people. Depending on the content of the false alert, other critical resources may become unavailable due to investigating the situation (e.g., a false bomb threat in a crowded stadium may draw more police and EMS resources than other incidents).
An attack via WEA may also be used as a diversion to render critical resources temporarily unavailable in pursuit of another mission or goal. Likewise, if the area of deployment were more targeted and the stakes of the false threat more serious, something like this could be used as a primary attack method. For example, an alert detailing imminent missile strikes in certain sections of New York City may be enough to cause destructive levels of panic.
 Either way, potential attacks on the WEA system are capable of turning normalcy on its head in a matter of seconds. Given the circumstances from the Hawaii incident, a successful, false WEA message may also discourage the general public from taking these messages seriously when they are legitimate, potentially resulting in more damage – this time from actual emergencies.
Either way, potential attacks on the WEA system are capable of turning normalcy on its head in a matter of seconds. Given the circumstances from the Hawaii incident, a successful, false WEA message may also discourage the general public from taking these messages seriously when they are legitimate, potentially resulting in more damage – this time from actual emergencies.
Conclusion
While this exercise is purely hypothetical, it is not to discount the vulnerabilities in a critical alerting system. The WEA system using less-secure LTE mechanisms is an issue that should be addressed. A potential solution is merely adding more traditional authentication-based messaging mechanisms. It is imperative that we, as an industry, continue to look at critical infrastructure for vulnerabilities proactively. While it’s impossible to know, the weaknesses in systems that we address today can very well save lives tomorrow.
References
Mead, N. R., & Woody, C. (2016). Cyber security engineering: A practical approach for systems and software assurance. Addison-Wesley Professional











